As cybercriminals get more advanced in their tactics, traditional 9-to-5 security technologies are becoming less effective at stopping them.
What does that mean for your business?
It means offering a 24×7 proactive cybersecurity solution is crucial.
To combat today’s cybercriminal advances, our team recommends Managed Detection and Response.
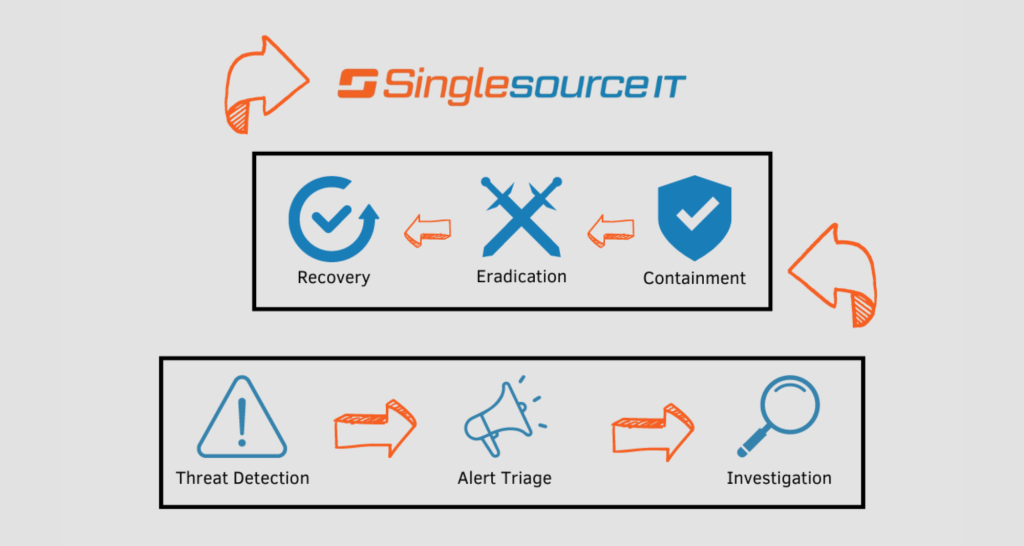
Managed Detection and Response (MDR) is a holistic approach to cybersecurity that combines technology, people, and processes to identify and respond to threats in real-time. MDR provides 24/7 monitoring of networks, endpoints, and cloud environments, along with threat intelligence and incident response.
At the core of our Managed Detection and Response offering is our team’s ability to provide organizations like yours with continuous visibility into their security posture. This is achieved using advanced technologies such as AI and machine learning applied to Security Information and Event Management (SIEM) and Intrusion Detection Systems (IDS).
Our MDR solution’s continuous monitoring allows for the detection of threats in real time, enabling a quick response to potential attacks. Cybercriminals have proven their ability to get around legacy antivirus and firewalls — MDR is the next step in protecting your company’s productivity.
To learn more about our MDR offering, download our MDR PDF.









 Protect Your Email with EasyDMARC
Protect Your Email with EasyDMARC

