December is filled with “Best Of” lists, with articles everywhere ranking the biggest tunes of the year, the highest-grossing movies, or the most-streamed shows.
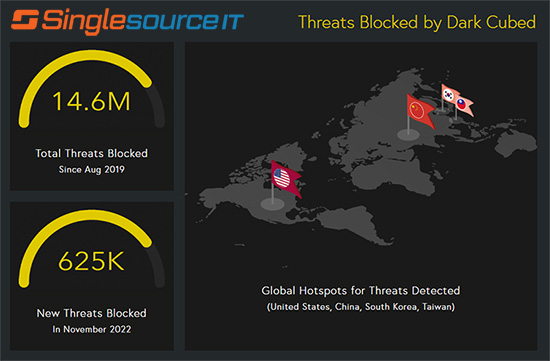
At Singlesource IT, we take cyber-security seriously, so when our partners at Dark Cubed send out their “Worst Of” Malware Report, we know we’ve got to take a look.
The end of 2022 saw a surge in Malware-as-a-Service (MaaS) attacks across the globe. MaaS is very similar to the legitimate industry of Software-as-a-Service (SaaS), which is probably something you use everyday. These are software packages that are sold by subscription, and are more likely to run in-the-cloud than on your personal device or corporate server.
Hackers have caught on to the business model, and now lease the tools needed to run turn-key cyber attacks, no coding necessary. While that lowers the bar to entry, it also means that there are trends and bigger targets that experts like Dark Cubed can focus on and defend against.
Here are the top three for 2022:
1. QakBot – This modular remote access Trojan is the new favorite among ransomware operators looking to purchase MaaS, with a 400% increase in activity at the end of 2022
2. Redline InfoStealer – This is another malware family widely used for credential theft and remote access, and the top source of stolen credentials for purchase on the Dark Web.
3. Racoon Infostealer – Yet another “Malware-as-a-Service,” Infostealer is connected to a suspected Ukrainian national running the Racoon botnet.
Click here for further details.
The growth in the MaaS industry makes it clear that has become increasingly profitable — but you don’t have to be a victim.
Make 2023 the year that you take your protection seriously. Schedule a consultation with us today to find out how our 100% Automated Threat Detection can keep your critical data safe, confidential, and out-of-reach.









 Check Out Our New 2022 Guide to Reducing Human Cyber Risk!
Check Out Our New 2022 Guide to Reducing Human Cyber Risk!