It’s no secret that cyber criminals are increasingly targeting small and medium sized businesses, but what do those generic “threats” look like? Our threat detection and blocking partner recently looked in detail at some of the traffic they’re blocking on SMB networks all over the world, and here are some examples of what they’re seeing (and blocking):

● A known phishing site in Germany connecting to the network of a State Regulatory Agency office in the southern US
● A host – located in the US – associated with brute force SSH attacks (the objective of which is to use the SSH protocol to execute commands on a remote computer) was blocked by Dark Cubed on the network of the offices of a small municipality in the southwest US
● An Iranian Telecom company’s address, identified for exploiting SQL server vulnerabilities was connecting to a K-12 school district in the southwest US
● A host located in China and associated with brute force attacks (automated attempts to identify weak passwords) was blocked on that same K-12 school district’s website
● A German-located device launching a Telnet open port scan and potential SNMP (Simple Network Management Protocol) attack against an Animal Hospital in the midwest
These examples were collected randomly, so there’s every reason to believe they are indicative of the kinds of threats facing our customers every day.
As we’ve discussed previously, we’ve added a service to our offering designed specifically to counter these common threats, and we’re excited to offer it to you and all of our customers.
Let me know when might be a good time to talk more about how we can expand our service to materially reduce your cyber risk with this compelling new technology.
Andy Fruechtnicht
Singlesource IT








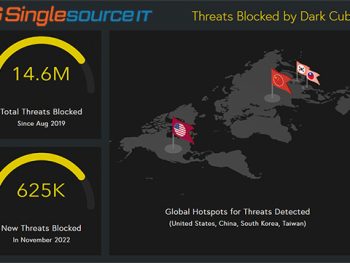
 Monthly Threat Reports from Singlesource IT
Monthly Threat Reports from Singlesource IT